| subject | Shared Hosting from Domain And Hosting Solutions |
|---|---|
| writer | Quinton |
| quintonhumffray@aol.com | |
| date | 24-07-02 19:53 |
| hit | 10 |
관련링크본문We all know that bettering the on-site experience of your internet site guests and reaching a greater search engine ranking are a precedence for you. To accomplish that, your websites have to be situated on a server, which is close to your potential visitors. Hence, we offer you the chance to decide on between three next-technology knowledge middle services situated on 3 completely different continents. Your choices might be: the Steadfast information heart in Chicago - should you need a US Shared Hosting service; our data middle facility in London - in case you want a UK Shared Hosting service; our Eastern Europe based mostly datacenter in Sofia, Bulgaria, in case you require an East European shared hosting resolution; and the information heart facility in Sydney - in the event you choose an AU Shared Hosting service. Your information heart choice doesn’t change the costs or the array of obtainable options. At any price, you’ll get: a 99.9% uptime assure with all cloud net hosting plans and internet hosting services, the most recent stable releases of MySQL and PostgreSQL, along with the chance to decide on your PHP version. There's nothing extra distracting than a chatterbox, except perhaps two chatterboxes, within the tasting room. Offer a short introduction. The host should give the tasters some normal details about what's in front of them. Pour small tasting parts. Wine glasses, one for every wine, needs to be set out in a semicircle in entrance of every taster. The bagged bottles (which have been numbered or lettered by somebody aside from the host) should be handed among the many tasters so each can pour a small sample (roughly two ounces). Consider buying a pouring disc, an awesome, inexpensive, reusable software that facilitates pouring in measured quantities with out dripping. Product of flexible heavy foil, these discs fold right into a funnel form and fit into the bottle opening. They come a number of to a packet and may be present in most wine stores. If desired, tasters' glasses could be lettered or numbered on the bottom with a wet-erase pen, available at most stores that sell stationery or office supplies. Because the pandemic began in early 2020, many travelers have turned to trip dwelling rentals as a secure possibility for a getaway with built-in social distance. A significant participant on this market is Airbnb. It connects individuals with places to stay and issues to do across the globe. The group is powered by hosts, who provide their friends with the distinctive alternative to stay like an area whereas traveling. You might have thought of providing up an extra room in your own home or placing your total condominium up for share on Airbnb. You would not be alone. If you have any issues pertaining to where and how to use bulletproof hosting buy, you can contact us at our own webpage. About four million individuals worldwide hold the esteemed title of "Airbnb host," welcoming over 800 million guest arrivals in nearly every country throughout the globe. If you need to meet individuals from all around the world and earn additional revenue, listed below are the correct steps to becoming an Airbnb host. Go to the Airbnb host web page and enter fundamental information about your itemizing with easy-to-observe immediate questions. A complicated phishing attack that exploits weaknesses in the legit websites of monetary establishments to make makes an attempt to trick people into handing over confidential particulars more plausible. A profitable use of Cross-site scripting will make it look like all of the transactions are being accomplished on the website of the actual financial institution or monetary institution. A hijacked Pc or server used to store all the personal data stolen by keyloggers, spyware or viruses. Criminal hackers prefer to keep their distance from this information as its possession is incriminating. Dead drops are normally found and shut down within a couple of days of the related phishing e-mails being sent out. Abbreviation for Distributed Denial of Service. That is an attack by which thousands of separate computers, that are often a part of a botnet, bombard a goal with bogus data to knock it off the online. DDoS attacks have been used by extortionists who threaten to knock a site offline except a hefty ransom is paid. Consequently, botnet attacks have steadily increased. Now they’re maybe essentially the most prevalent cybersecurity threat. €¢ and random, which is commonly P2P/peer-to-peer, dynamic and communicates across multiple paths, making the cybersecurity team’s job much more durable. That means that C2 botnet attacks are highly resilient. And all that aforementioned selection lends itself to quite a lot of malicious activity - denial of service assaults, spamming, identity and knowledge theft, brute drive assaults, and traffic monitoring. Just as we name the units in a botnet “bots†(or “zombiesâ€), you can name the attacker who controls them a “bot herder†or “botmasterâ€. As if individual bot herders didn’t pose sufficient menace, many are also successfully bot brokers. They rent botnets to other cybercriminals to allow them to achieve control of compromised machines. Shutting down these operations might be difficult, however each success brings great positive factors to your entire Internet neighborhood. Learn how to Manage Threats from C2 Servers? 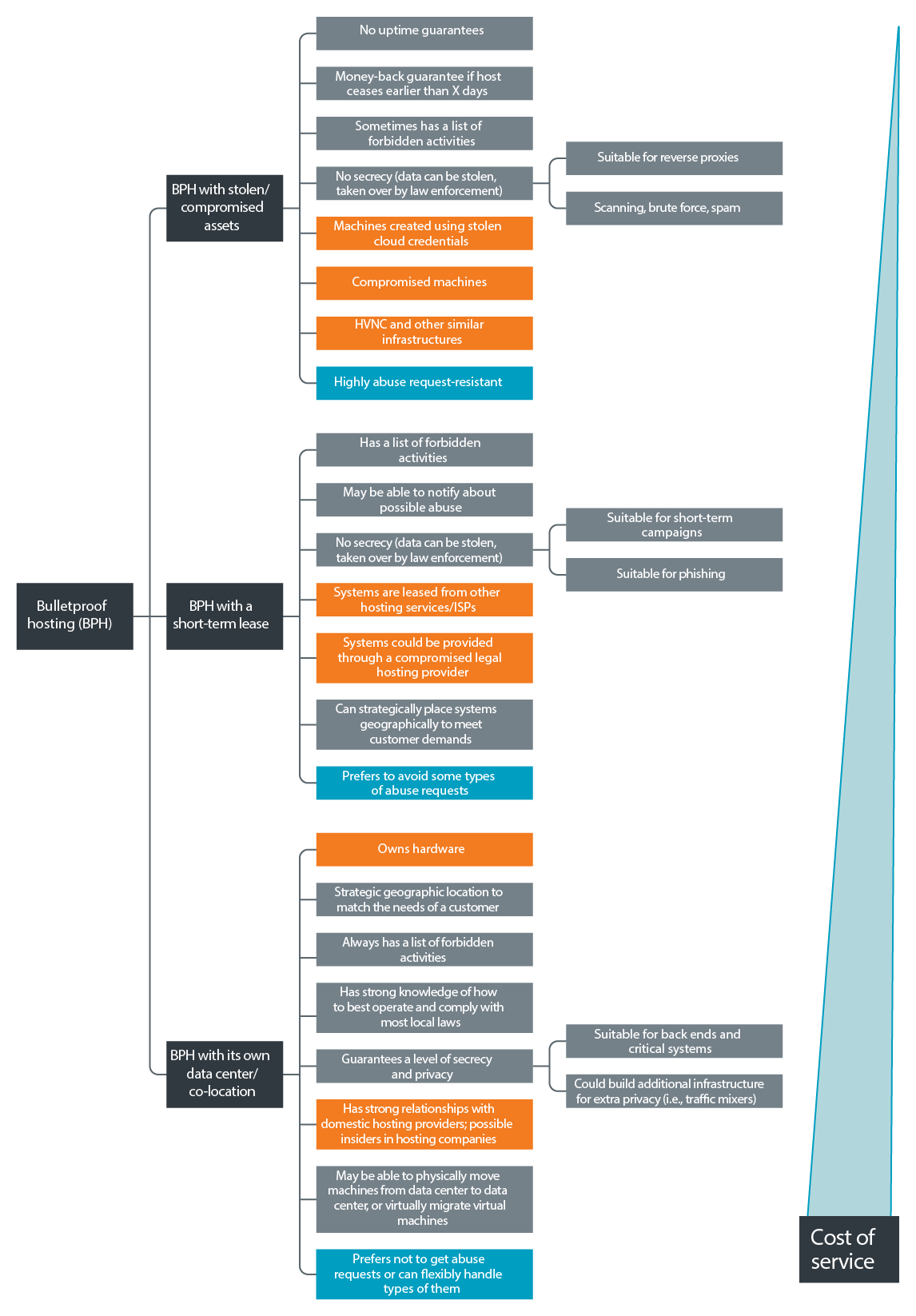 |
|
댓글목록
등록된 댓글이 없습니다.